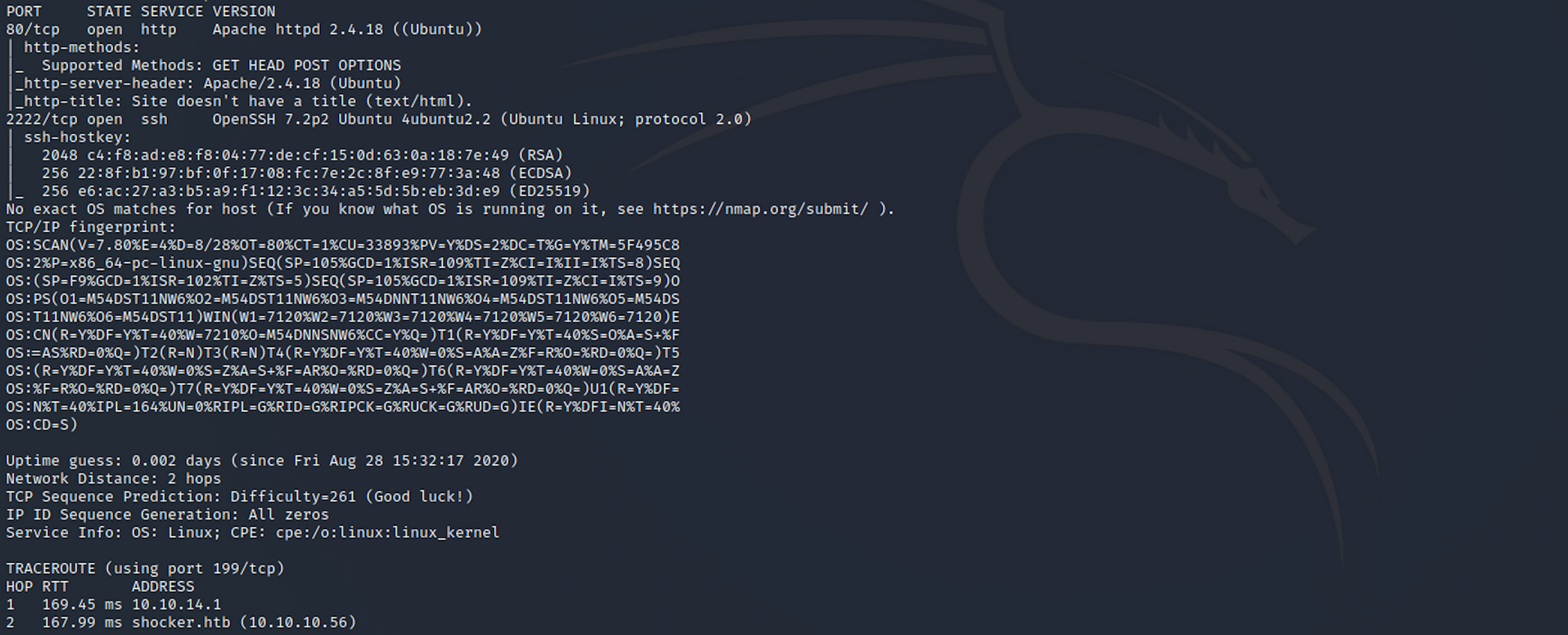
GitHub - hktalent/scan4all: Official repository vuls Scan: 15000+PoCs; 23 kinds of application password crack; 7000+Web fingerprints; 146 protocols and 90000+ rules Port scanning; Fuzz, HW, awesome BugBounty( ͡° ͜ʖ ͡°)...
![Deploying CIP Security within a Converged Plantwide Ethernet Architecture - CPwE CIP Security Design Considerations [Design Zone for Industry Solutions] - Cisco Deploying CIP Security within a Converged Plantwide Ethernet Architecture - CPwE CIP Security Design Considerations [Design Zone for Industry Solutions] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/380001-390000/386001-387000/386006.jpg)
Deploying CIP Security within a Converged Plantwide Ethernet Architecture - CPwE CIP Security Design Considerations [Design Zone for Industry Solutions] - Cisco