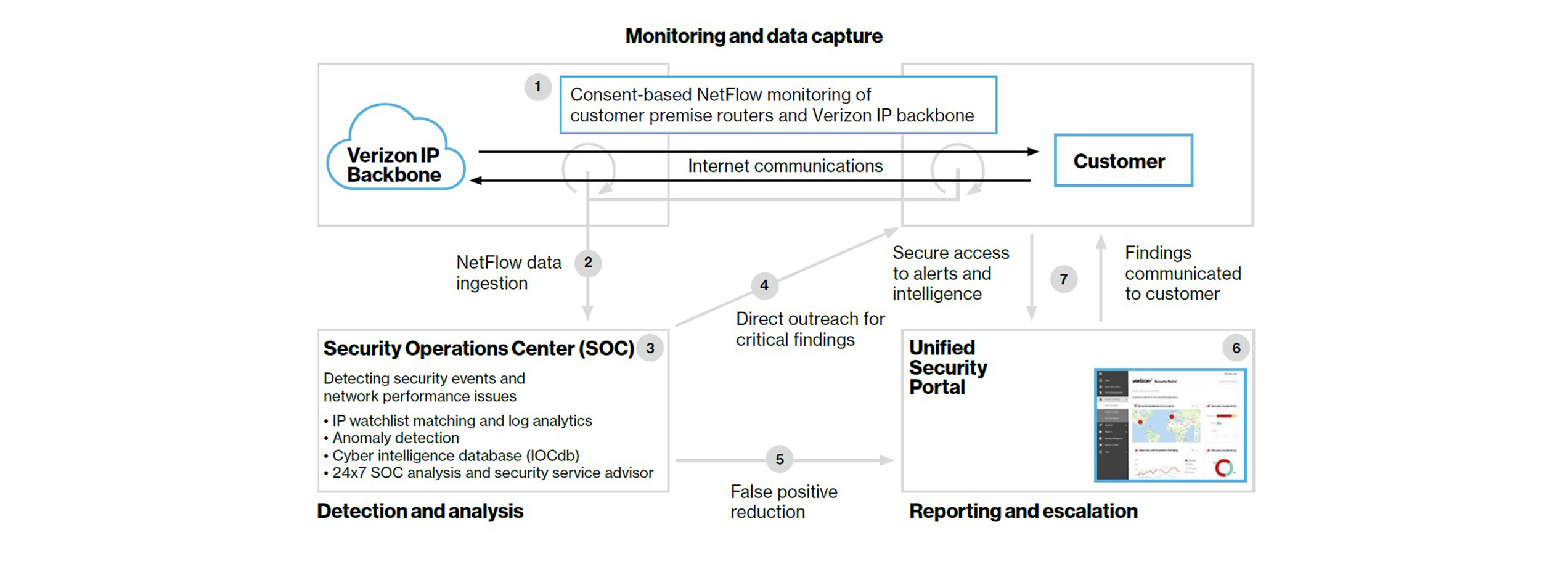
Threat Analysis System - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Cyber Threat Intelligent (CTI) dataset generated from public security reports and malware repositories | IEEE DataPort
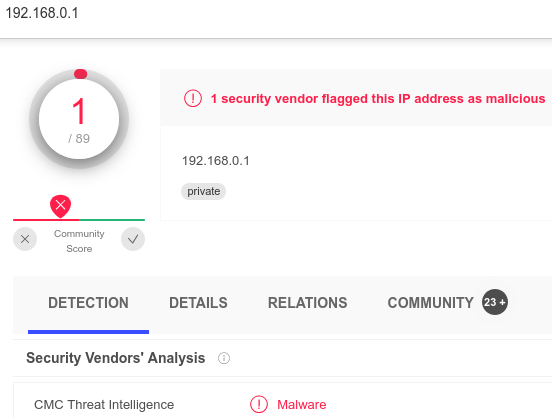
MalwareHunterTeam on Twitter: "TIL about some very malicious IP addresses thanks to Comodo and CMC: 127.0.0.1 8.8.8.8 1.1.1.1 192.168.0.1 Block them all!!! 😂 https://t.co/93P5S45FdS" / Twitter

IP Reputation Analysis Report - August 2017 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Threat Hunting: How Group-IB's Graph Network Analysis helps predict cybercriminal activity, even before it happens | Group-IB


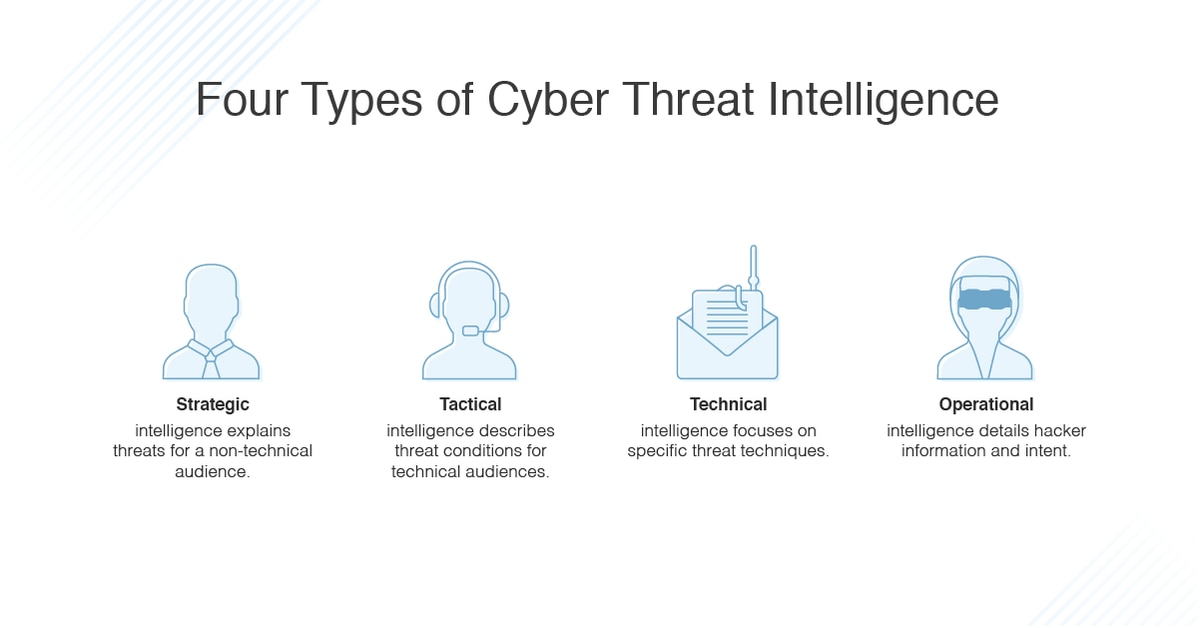




![What Is IP Reputation And How To Check It? [Updated 2022] What Is IP Reputation And How To Check It? [Updated 2022]](https://www.vpnranks.com/wp-content/uploads/2022/02/brightcloud-ip-detection.png)